
Every enterprise today is consuming a large amount of sensitive information in some way or form. This data holds value and is an integral part of an organization. To secure this data, you need the right set of tools to discover sensitive data within your environment. This is one of the biggest challenges firms are facing right now! This article will provide you with all the important factors that you should consider while choosing the right sensitive data discovery tool.
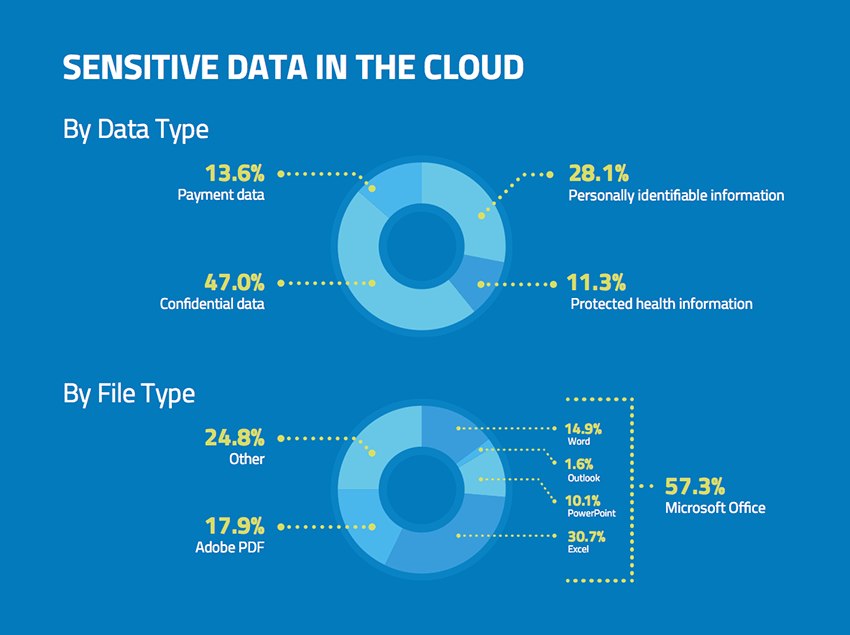
Source: McAfee
First, you have to understand WHICH data is sensitive!
Big organizations like Goldman Sachs, HSBC, etc. collect and store petabytes of data. Not all data that is stored on your server or cloud is sensitive.
Sensitive or confidential data is the information stored on your database which contains important information about your users or clients, such as credit card details, scanned copy of confidential documents, contracts, SSN, passwords or PINs to important accounts, etc. This information is the most vulnerable to security threats.
According to research – “HIPAA regulation has up to 18 identifiers of sensitive data that must be protected”
This data can either be in the structured or unstructured forms. The data discovery tool should be able to discover this data, regardless of its format in order to secure it.
We hear about data breaches increasing every year, and countries are taking precautions by introducing various security compliance measures like CCPA, GDPR, HIPAA, and others. This is the reason sensitive data security tools are in demand these days. Organizations want to identify sensitive information in their data sources and secure it to prevent advanced security threats.
“Data is a precious thing and will last longer than the systems themselves.” – Tim Berners-Lee, the official inventor of the World Wide Web.
The best sensitive data discovery tools access the information stored on your server or cloud storage and secure the information using various encryption techniques.
Here are some tips to help you find the right sensitive data security tools according to your business needs:
#1 Research
Researching sensitive data discovery products available in the marketplace is a challenging task, as a lot of great products are available these days. Picking up a good tool is very important for your data. Understand who are the top players in the marketplace offering sensitive data discovery tools.
- Does the tool offer all the primary data discovery functionalities like processing different formats of data?
- Are clients happy with their tools? Do they provide good feedback/reviews about the product?
- How frequently do sensitive data discovery tool vendors upgrade the features to support the latest technologies?
- Does the cost of the product justify the features that it offers?
The aforementioned are the major queries to be answered by your market research team to find the best tool to discover your sensitive data. Performing deep-dive research and considering all the important parameters are mandatory when it comes to safeguarding your confidential information.
There are a few top software listing sites such as Capterra, G2Crowd and Trust Radius. They enable you to run a comparative feature analysis of products to choose the one best suited to your business.
Companies register their enterprise data security products on review sites where the customers can share their product experience. It helps users find better sensitive data security products for their firms.
#2 Feature requirement analysis
Analyze your own business needs and the outcomes that you expect from the tool. You should understand your organization’s data sources and classify the sensitive data you really have. Connecting with the core teams and stakeholders to understand the requirement in detail would help you decide upon what features the tool should possess.
Technology: The data discovery tool should be able to tag your sensitive data and suggest the right method to secure it. AI-powered tools are efficient at discovering sensitive information and classifying it by adding the right tags to the data. The machine learning mechanism in these tools analyzes the manually updated fields and updates the patterns accordingly on their future scanning processes. For example, the enterprise data security product- Kogni uses artificial intelligence technology to find sensitive information in the cloud.
Security compliance: It should be compliant with evolving data regulations and policies. Expert data discovery tools such as Varonis and Kogni support all the prominent security compliances like HIPPA, GDPR, CCPA, PCI, FERPA, and others.
Data classification: Does the tool have an automated or manual process to classify your sensitive information? Does it offer any advanced rule-based classification? For example, the Imperva tool allows a wide range of data classification techniques.
Monitoring: It should be able to discover potential risks or advanced threats to your sensitive data. DataGrail is a tool that provides continuous data monitoring, identifies potential threats, and generates alerts to secure data from future data breaches.
Access management: You should know the user access management of the tool. Who will be able to access the data? Who will handle the sensitive data? All these questions should be answered before you opt for the product. Tedsystems is the market leader for protecting sensitive data with exclusive access control.
Make sure to choose a software that leads in all these areas and provides an all-in-one integrated solution. Kogni is fully equipped for all your data security and data privacy needs. It is an AI-powered data security tool that is fully compliant with a best in class data monitoring feature that generates alerts to assist with data loss prevention.
#3 Reporting mechanism and support
Analyze the reporting mechanism of the sensitive data discovery tool you are planning to buy for your organization. Various tools offer a comprehensive dashboard that allows users to view all their sensitive data in one window and understand how it is being processed. It indicates the number of sensitive data files present in a database and the techniques used to encrypt the confidential information.
Some market leaders in sensitive data reporting, such as InetSoft, Kogni Enterprise Data Security Tool, Veracode, IBM® Security Guardium, etc. offer top-notch reporting dashboards to prevent advanced security threats. They provide actionable insights to identify a potential threat to the confidential information in the data sources and prevent the event occurrence.
Does your sensitive data discovery tool vendor offer you the right support?
It is a very important, and often neglected question to be answered before picking up any data discovery tool for your organization. Understanding all the ways vendors can support you is a necessary aspect. Will they provide product demonstration, training, product explainer videos, webinars, and the right expert support at any given point?
For example, Veracode offers a detailed tutorial on how to implement it, IBM® Security Guardium offers live training and dedicated support to each client, Whereas Kogni data security offers all the email, phone, webinars and chat support to the customers with dedicated expert resources. So, when you consider a data discovery tool, it is important to evaluate the post-purchase support procedure they have.
Conclusion
It is very easy to pick any sensitive data discovery tool for your company. While some product vendors focus on acquiring new customers, others focus on maintaining their relationship with their clients and providing the best customer experience. Choosing the right solution with all the necessary features, the right support, and the right price is a very important requirement!

